Discrete Authorization for Capacity Sharing
The network operator has to verify whether the supplicant of a shared connection is indeed allowed to join the network, which is addressed in our solution by means of multi-time digital signature schemes.The whole authorization process considered in the actual scenario is depicted in the figure 1.
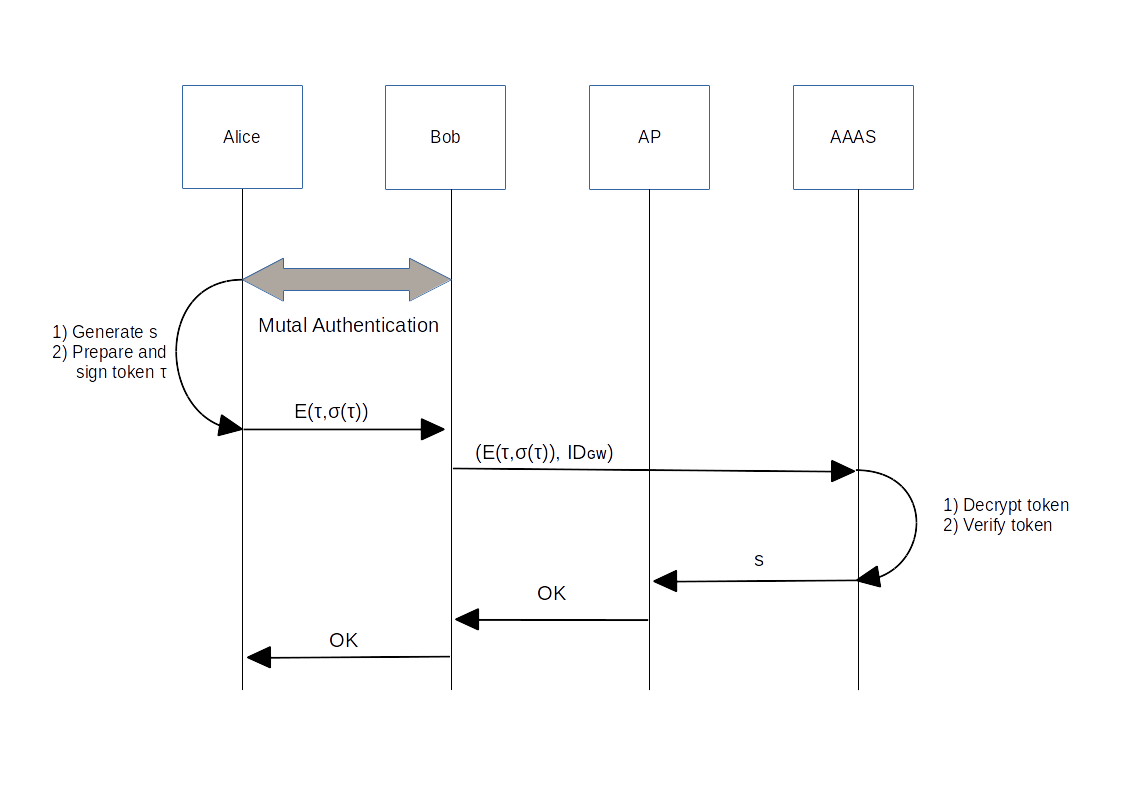
After Bob’s admission has taken place at the network operator’s Authentication, Authorization and Accounting Server (AAAS), he may share, as a gateway, his connection with Alice. In order to join the network, Alice generates an ephemeral key s and an access token τ . Thereafter, she encrypts an access token τ with the AAAS' public key and signs the ciphertext with her N-time signature key, obtaining (E(τ), σ(E(τ))). Alice then sends (E(τ), σ(E(τ))) to Bob, who appends the ID claimed by Alice during the mutual authentication step to the outgoing message and forwards it towards the AAAS.
After the reception of (E(τ), σ(E(τ)), IDGW) by the AAAS, it decrypts the payload of Alice and performs the token verification process. If the verification is successfully accomplished, the AAAS informs the AP of the acceptance of Alice and provides Alice’s ephemeral key to the AP, which will inform Bob that Alice’s request has been accepted. Otherwise, the AAAS informs Bob that Alice’s request has been denied.
Proof of Concept (PoC)
In the capacity sharing scenario (figure 2) Alice gains access to the Internet through Bob's connection. Since the ISP is able to identify Alice over Bob's connection, it can provide specific QoS to each one of them. It allows the ISP to increasing Bob's connection bandwidth, in order to maintain data throughput to Bob and also convey data to Alice.
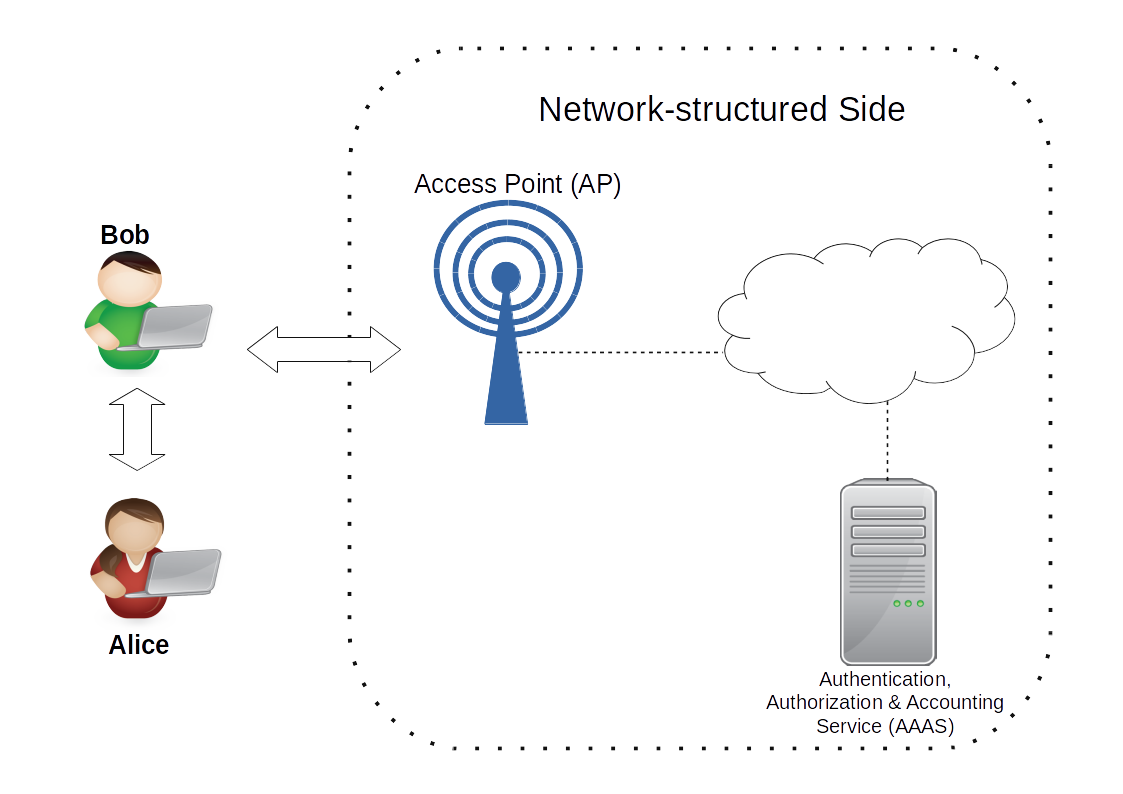
Figure 3 shows the considered scenario in this PoC. A proxy has been put in place instead of the access point, since it is beyond the scope of this PoC to develop a de facto access point. Although both concepts are slightly different, this approach has no impact to our PoC, since both are gatekeepers of the Internet.
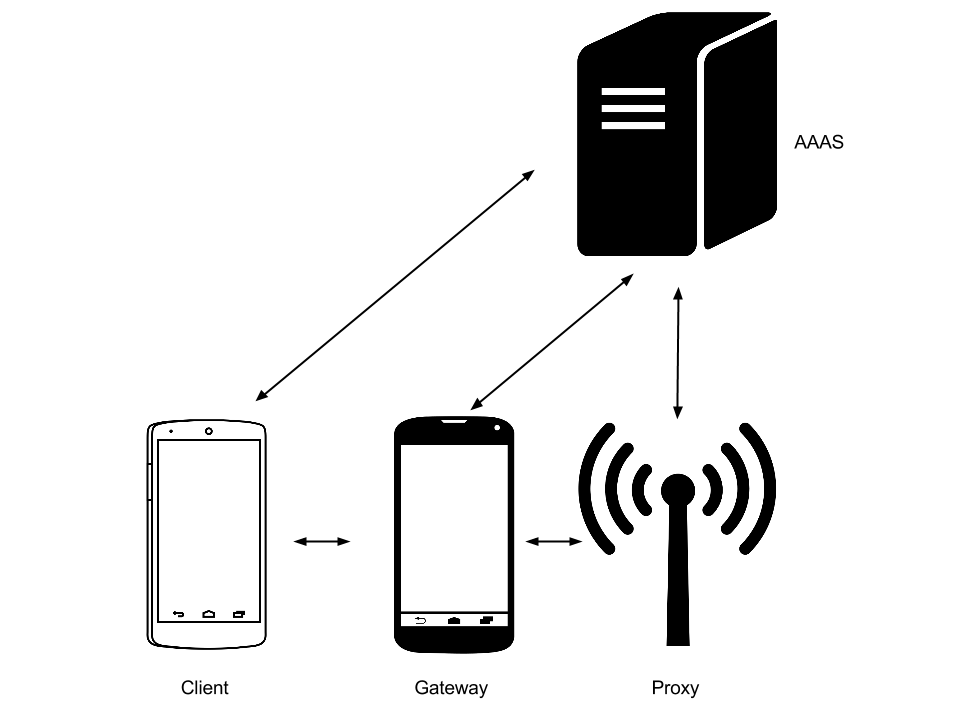
Alice and Bob from figure 2 are respectively represented as client and gateway in figure 3. For them, we have developped an Android App, which communicates via Bluetooth between them and, in the case of the gateway, through WiFi or GSM with the Proxy. The main use case is to grant the Client limited access to the Internet (1MB) through Bluetooth, after the successful verification of their access token.